
Welcome to my write up of the TryHackMe room called Sakura by the OSINT Dojo!
Info From Client:
The OSINT Dojo recently found themselves the victim of a cyber attack. It seems that there is no major damage, and there does not appear to be any other significant indicators of compromise on any of our systems. However during forensic analysis our admins found an image left behind by the cybercriminals. Perhaps it contains some clues that could allow us to determine who the attackers were?
Info left by the Attacker:

So we received this calling card saying that our client was “Pwned” on the web browser. So now our goal was to find the person responsible for it. But how should we proceed? We have a few ways, But my method of checking for this info was checking the source code of this webpage.
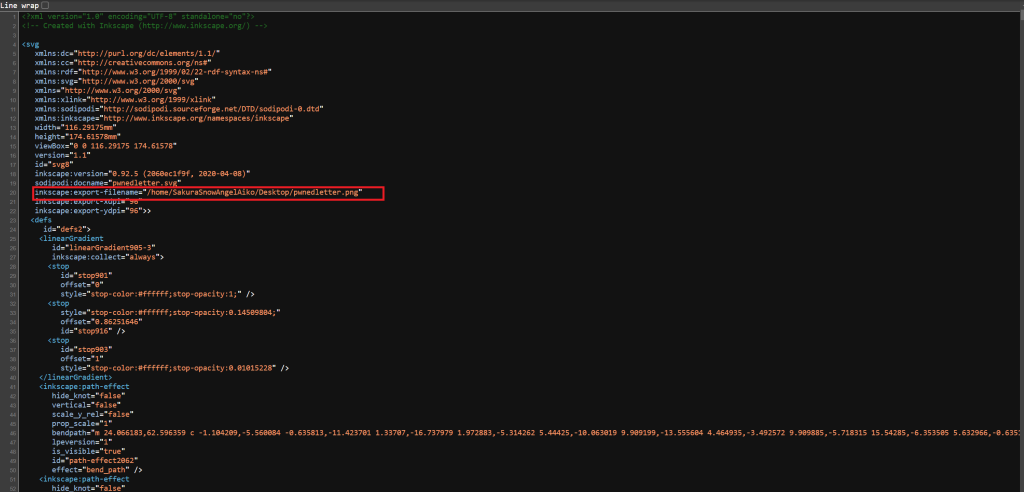
We can find the username “SakuraSnowAngelAiko” This is very valuable information because now we can further enumerate this person!
Next lets move onto finding this attackers identity. We are now tasked with finding their email address!
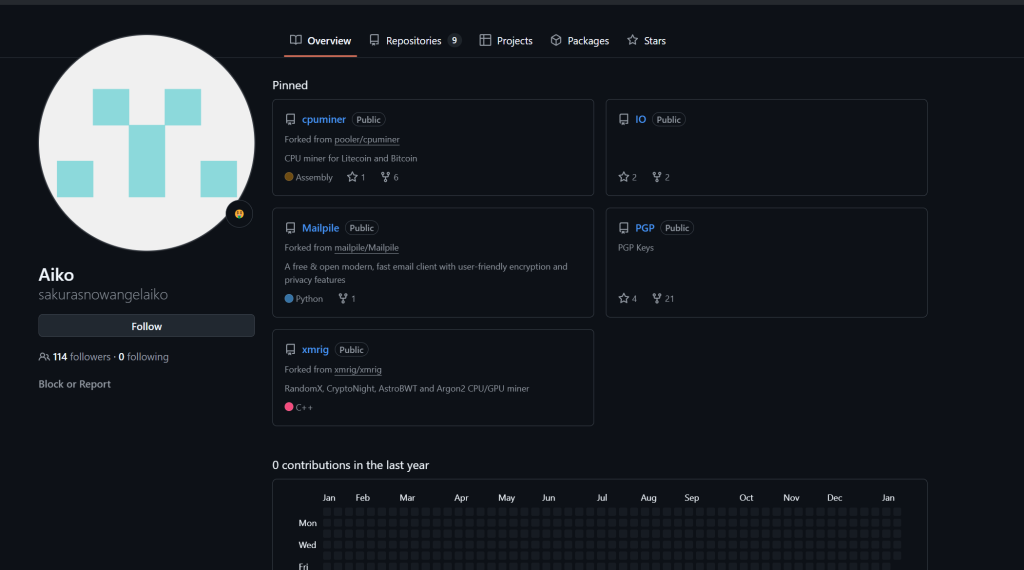
So i found their github by entering their username into google
Next I found a repo she left behind that left her PGP key
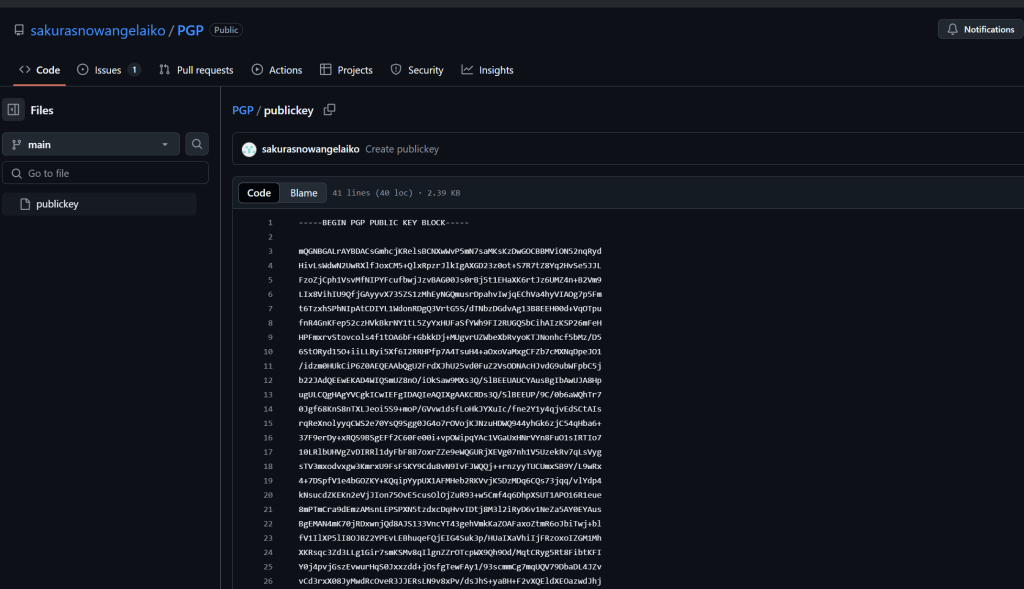
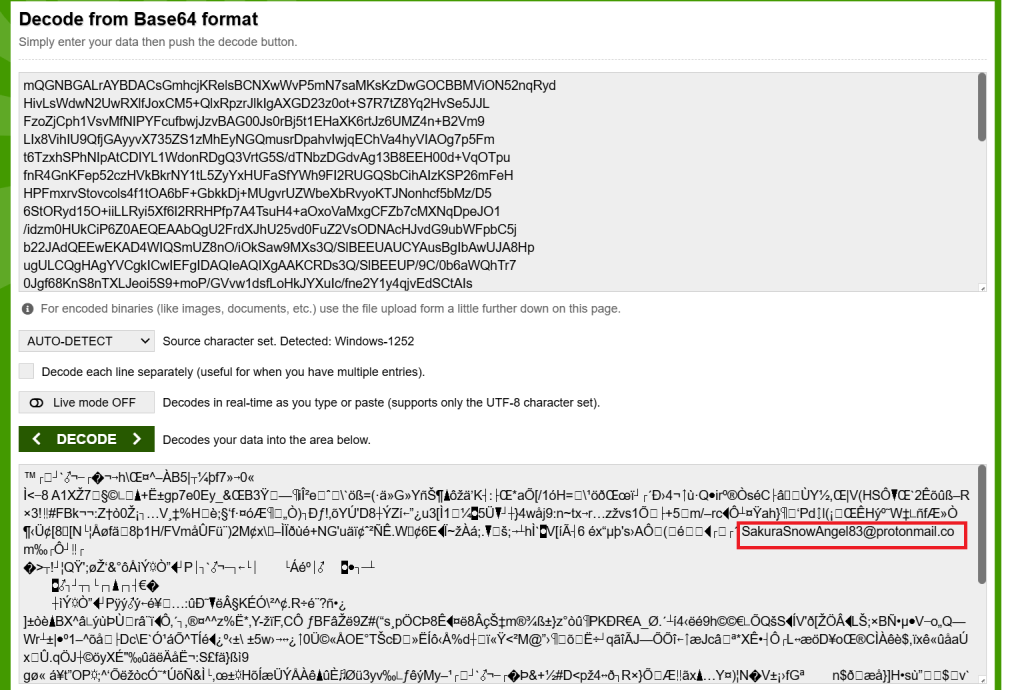
I decided to decode this pgp with a base64 decoder and to my surprise I found their email
Now we must uncover their name, So for this method I didn’t do anything special. I went back to google and found she had a twitter profile!
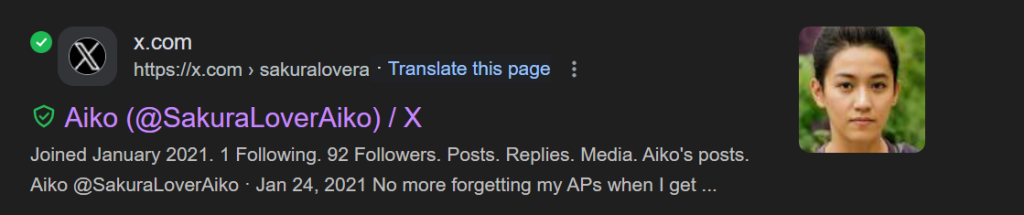
This user left us a lot of different clues, intentionally or unintentionally but she didn’t take into an account where she tweeted a message to her personal account
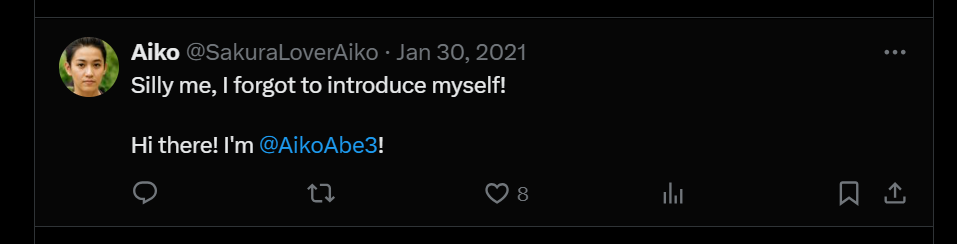
which left me with a last name! This was a big find so now if wanted we can dig deeper into the attacker, But our client only wanted specific information, So lets move on!
Update:
I recently got word from the client that something had changed
Client: It seems the cybercriminal is aware that we are on to them. As we were investigating into their Github account we observed indicators that the account owner had already begun editing and deleting information in order to throw us off their trail. It is likely that they were removing this information because it contained some sort of data that would add to our investigation. Perhaps there is a way to retrieve the original information that they provided?
So This was quite an interesting turn of events, it almost feels like they left information intentionally for us to obtain. None the less the show must go on.
So next our client wanted to know what cryptocurrency our attacker was using to find some more leads.
I went back to the Github page and found something very interesting.
I found something labeled “ETH” which is short for Ethereum, so I decided to investigate this further
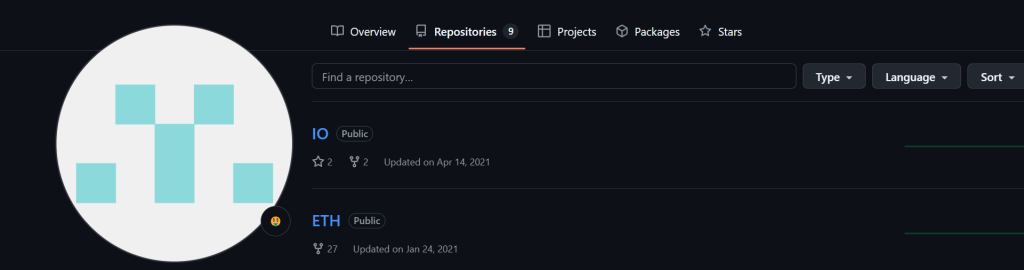
I only found a generic script which I thought at first was a dead end until I decided to search the history of this repo.
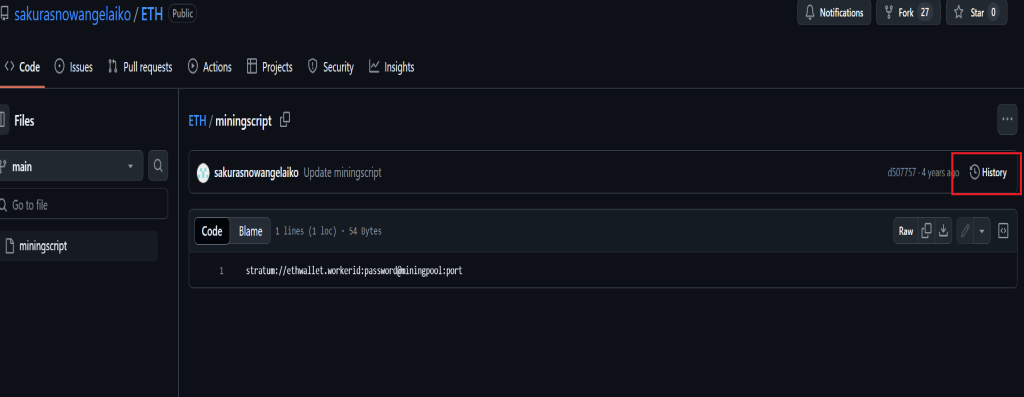
I see there was a commit change and decided to investigate further
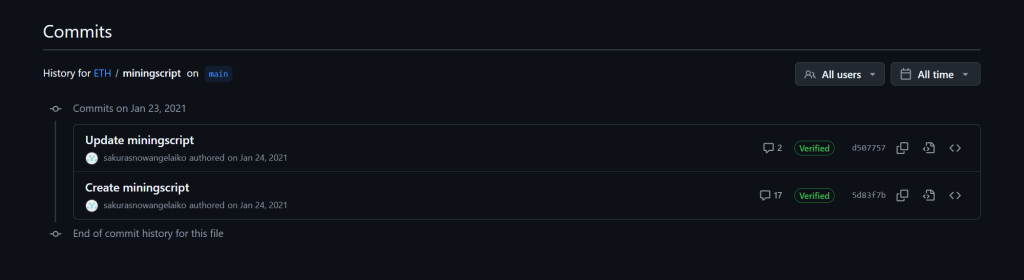
And sure enough I was able to find without a doubt that this person was potentially mining Ethereum and I happen to find her Ethereum wallet address, this was a big find!
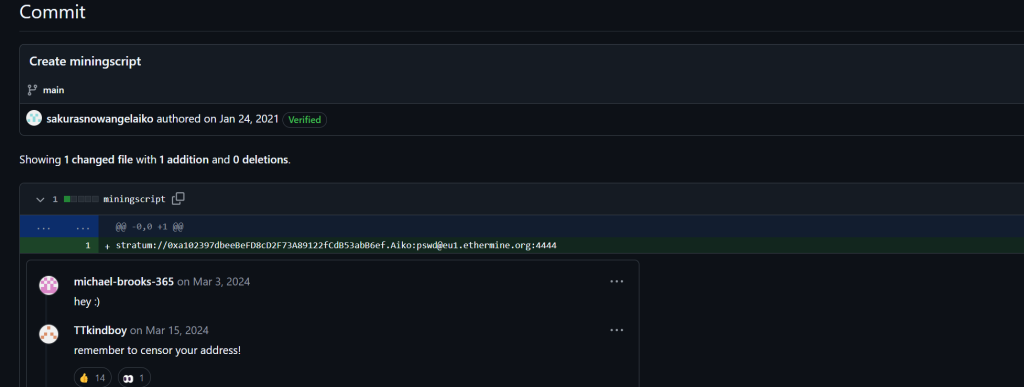
We also noticed they were using Ethermine, which is vitally important for our investigation.
After finding this great discovery I was tasked with finding out if they used any other currency to see if they were covering their tracks
So I decided to use our trusty website called etherscan and use their address to find any transactions
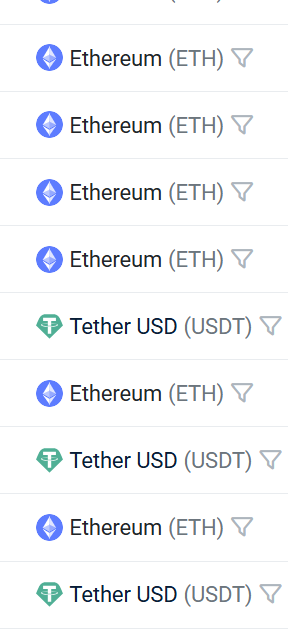
We can see there were a few transactions using Tether, which was interesting! So far our client was quite happy to see we started to piece the clues together to see if we could find this attacker.
But…the client started to get scared because the attacker was onto me and sent a threatening message on twitter.
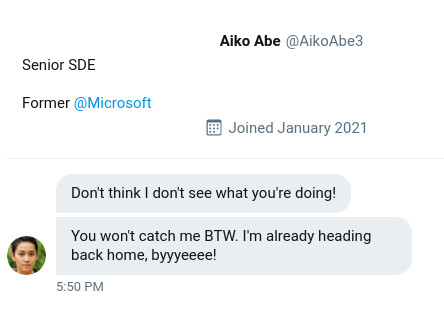
At this point the client was really worried and wanted to know their twitter handle. So luckily for us, we had already found that in a quick google search

After this finding I found the account I noticed some interesting tweets from them.

At this point I dont know if this was deliberate or if they really didn’t care. None the less we decided to follow this trail. I noticed it could potentially come from a dark web site. So I decided to take this information and look for it on the dark web.
So when i queried the hash above I found a deep paste bin and this was the result
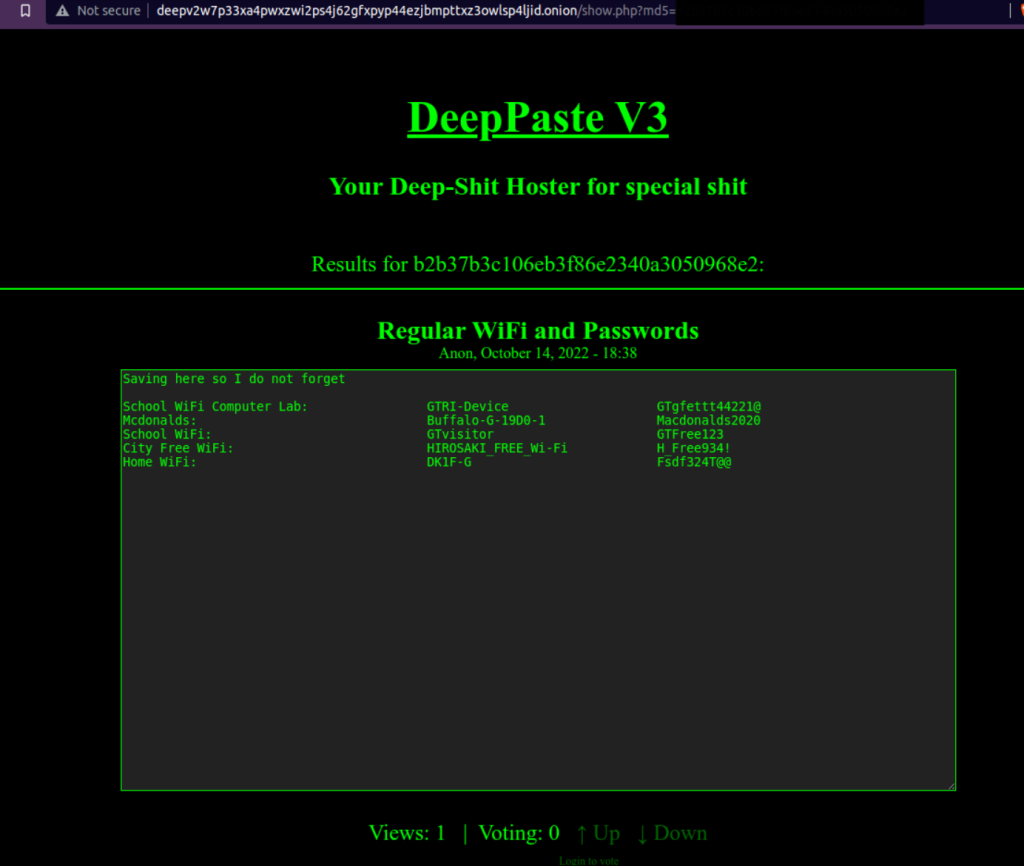
This was the critical turning point in the investigation because I found critical information about this person. So now that I potentially had some ssid’s and potential passwords it was time to use our good ol trusty tool Wigle.
So i decided to do an advanced search on their home wifi network, I took the potential SSID from this list and…
Bingo! I found a match
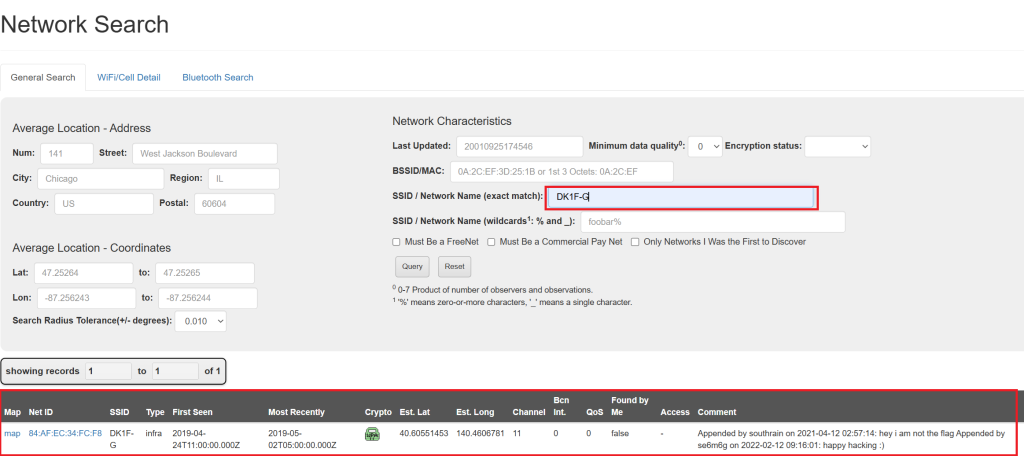
This was important because I directly know where this person was located! Next I pulled up the map and found a close whereabouts where she is from
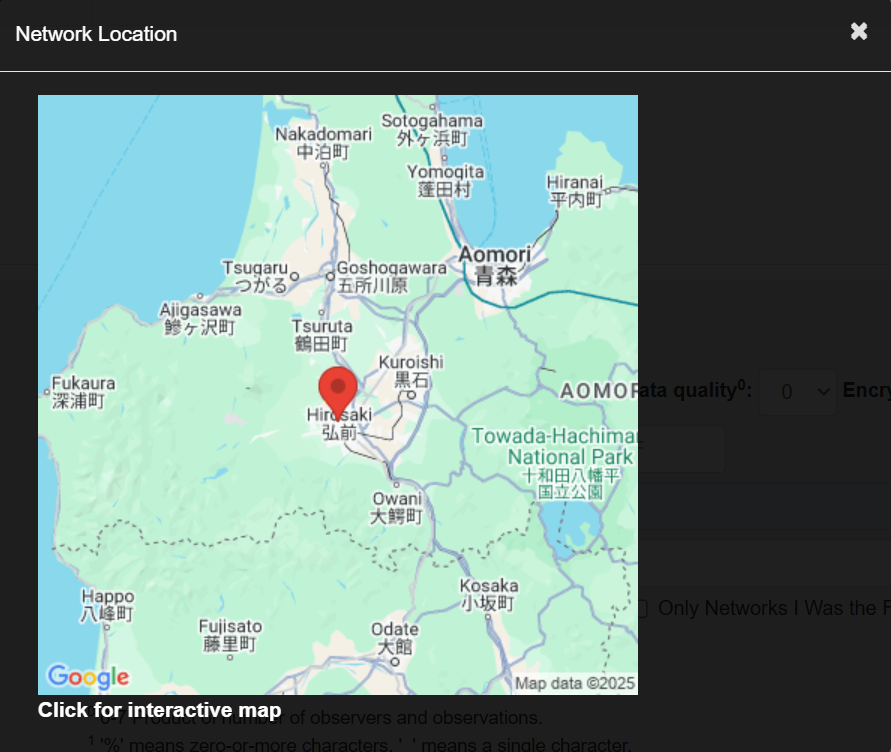
Now I could see where this connection came from and it located in Hirosaki Japan! Now we have direct evidence of who this person is and where this person was from! This was a huge found for me.
So we found out this person was heading back to Japan, But she left us some clues where she could potentially be and hopefully we can find her!
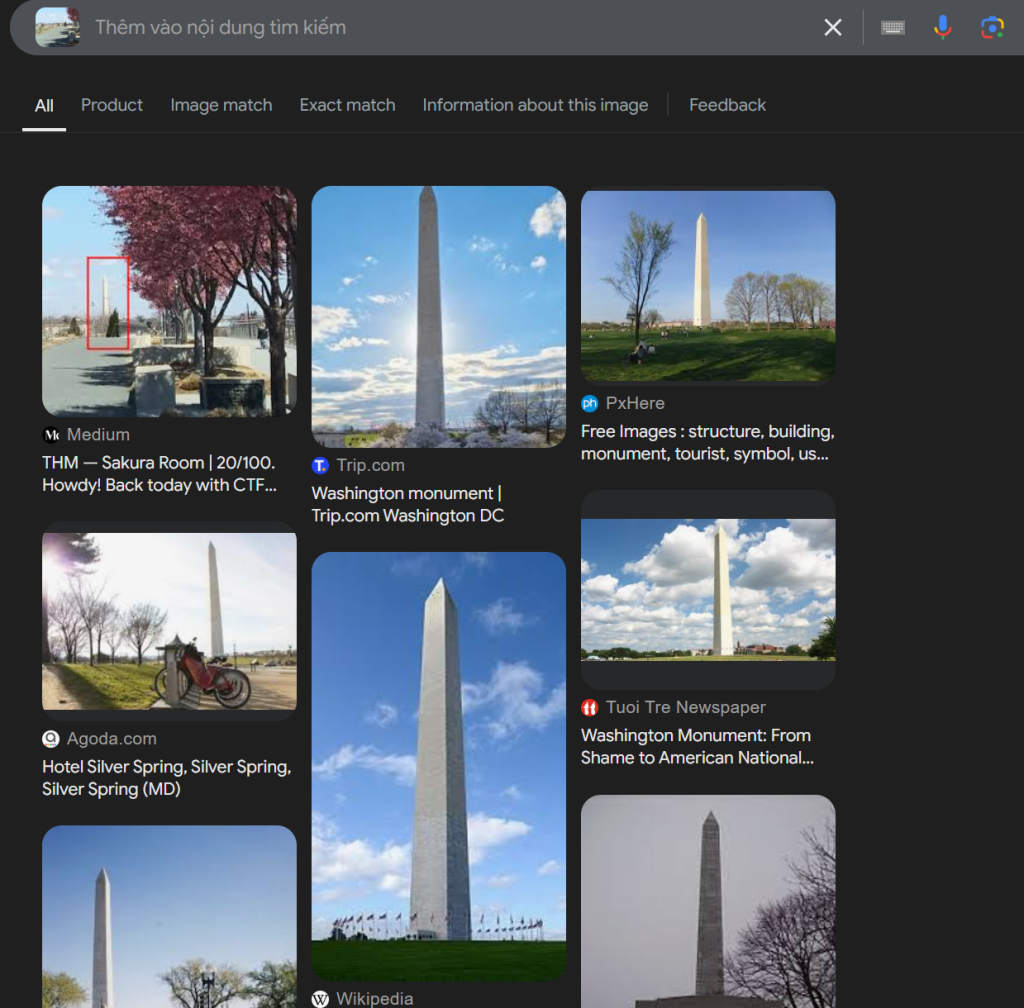
So when we looked back at her twitter feed. We saw a photo where she was around that time

I noticed something special in the background. It looked like a landmark

We did a quick reverse Image Search and I found this monument was in Virginia and was the Washington Monument! Wow what a find
So I decided to find the nearest airport near the Washington monument
And a quick google search revealed that the nearest airport was
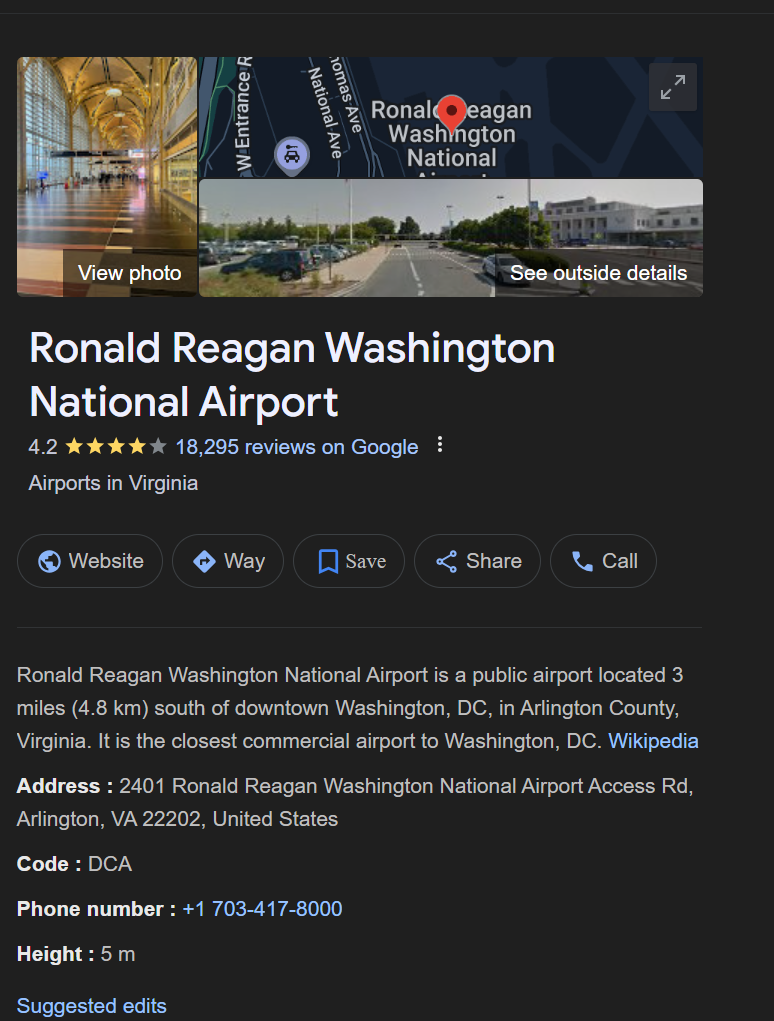
Which its airport code was DCA. This was a big breakthrough, we were hot on their trail!
we wanted to confirm some information to prove it was them, so we went back to twitter and this saw tweet.

If you notice in the image it says “Sakura Lounge” (Ironic) at JAL which is for Japan Airlines. So if we do a quick search we can find that Sakura lounge was in Haneda Airport, and their Airport code was HND.
If we decide to backtrack a bit. We can find this tweet, and it shows us a map of some sorts. Very interesting

My next step was to look up google maps and use the 3d view to see if I can replicate this photo and I find and out this location
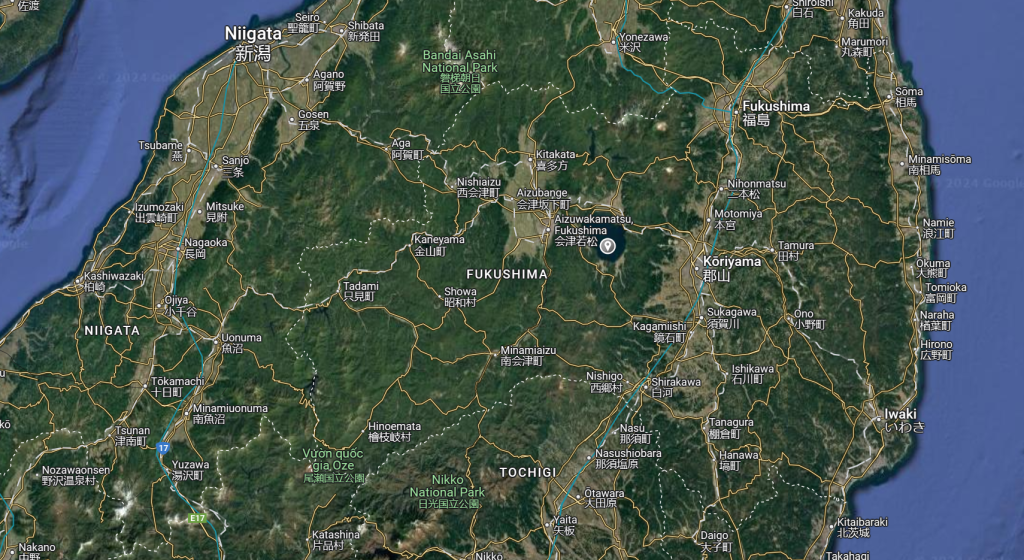
Looks like they were near Lake Inawashiro!
So in the end we were able to positively Identify the attacker as Aiko Abe! Now I wrapped up the investigation and gave all information and evidence to the client!
This concludes my walkthrough of the Sakura Room by the OSINT Dojo!
Thank you for reading and Happy Gathering
